security decision engine
AOE (Aspect-oriented business data encryption)
Software-defined Perimeter (SDP)
Secure network tunneling
Lightweight trusted computing technologies
New-generation security Sandbox technology
User behavior risk management

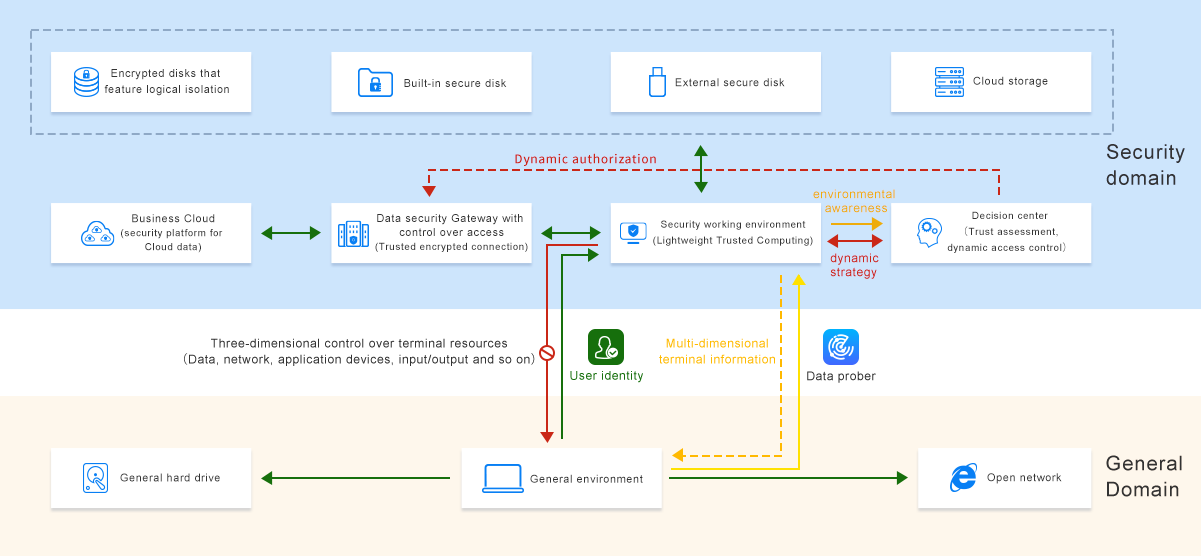
The enterprise terminal business operation security and information asset protection system creates a secure working desktop that is isolated logically at the user’s terminal by taking advantage of the zero-trust architecture and deep kernel filtering technology, trusted computing and encryption technology.

The gateway with control over access to the data is a system for transparent encryption and forwarding of communication data, which can enable the terminal to control the minimal and identity-based access to the business system effectively and precisely.

Dynamic masking and audit of data covering users’ information have been realized with fine-grained encryption of business system data. At the same time, employing a sandbox system to isolate business system data directory and precisely controls the access of applications to the sandbox data, while auditing, recording and synchronizing the backups for emergencies.

Secure Cloud storage eliminates the security risks brought by windows sharing including failure to control authority and inability to audit. Not only does it feature the same as but more powerful functions than windows sharing, but also it provides extra functions including offering access to authorities, confidentiality and logs. With no sharing loopholes, Secure Cloud storage avoids being encrypted for blackmail.

With a full record of and complete traceability to users’ behaviors, it can proactively target potential risks, realizing visual management of internal threats and risks. As such, it’s able to improve the internal security environment of a business by identifying responsible person instantly when risks emerge.

Based on user behavior analysis and big data technology, a work efficiency analysis system, according to the structures and businesses of an enterprise, divides business operations and non-business operations conducted by personnel from different positions. By doing so, supervision of personnel, analysis on work efficiency, and quantifiable management of work saturation of personnel have been realized.
Implementing software whitelisting, mandatory encrypted storage of business data, configuration segment and privacy protection, peripheral management, printing control and avoiding illegal processes communication, screenshots and screen recording. Data can only be exported with approval at the secure desktop.
Implementing identity-based login, allowing access to business systems only from a secure work environment, providing VPN and DLP, and building trusted network security domains based on access control policies.
Preventing risks from moving laterally and data theft (file and hard drive copies) within IT operations and maintenance, and achieving business-level disaster recovery;preventing internal and external attacks and insiders’ overstepping their authorities by realizing database encryption, dynamic masking, and audit.
With encrypted system transmission and encrypted network traffic, file sharing and internal email exchange are allowed between users of the same server within a secure working environment, and encrypted sending of public network files is allowed as well at WeChat and Dingding.
Getting offline access to log in to the secure work environment offline. Encrypted storage, controlled export and segment policies are still in effect while offline but data export is unavailable offline.
It targets threats and risks from within, realizing comprehensive behavior recording, behavior risk monitoring, behavior auditing and traceability, and work status monitoring.
Autonomous and controllable with leading security architecture

Perfect functionality with high standardization

Overall-secured data with network protection business

Impressive user experience with OS native style

Good scalability with platform-level products

Simple to implement and convenient to operate and maintain with deployment and initialization time less than 30 minutes

Lower cost and higher efficiency with VDI cost reduced by over 60%

Lightweight and trustworthy computing brings low resource usage with CPU usage lower than 3%